Recently, I was asked how to automate a process to request and approve external users having access to content inside an Office 365 Group. I am documenting an approach to solving this scenario using Microsoft's Cloud services in a series of blog posts. Each post will address part of the scenario from a different perspective and will discuss different technologies. The series contains the following posts:
- Overview of scenario and technologies
- Administrator - Configure tenant policies for groups and sharing (this post)
- End User - Make requests to add external users and monitor status
- Manager - Review and process requests
- Developer - Fill gaps in process via custom web service
Tenant Policies for Groups and Sharing
Adding an external user to a group is quite simple. In the web interface for Groups, when viewing the list of Group members, the context menu has an option to "Invite others." This option will initiate the Invitation flow for adding External Users to the directory and the group.
However, inviting external users to share content is not a simple process in some organizations. Since these users are not employees, their computers and email accounts are not under control of the organization. This means typical corporate solutions such as anti-virus and encryption may not be present. Any content in the group can be copied to a location beyond the control of records management and data loss protection. These issues are big stumbling blocks.
In some cases, these issues can be mitigated by applying policies and procedures to control the sharing process. Approving requests following some known criteria is common:
- Is the external user part of an organization with an existing business relationship?
- Is the account a corporate account, or a consumer email service?
- Can I get the external user to click on a policy acknowledgement page?
Working within these constraints is possible, and some Office 365 configuration will help enforce policy settings. These configuration settings are discussed in this article of the series.
Scenario Requirements
The scenario described in this series has a few requirements that inhibit the use of groups in the out-of-the-box configuration:- Invitations to external users must be approved.
- External Users must view and acknowledge a policy page.
The solution described in future articles will meet these requirements. In addition to building the solution, the default group configuration must be updated to restrict the invitation of users.
Group Settings
There are many settings that apply to Office 365 Groups (and Teams). I will discuss only those that apply in this scenario. For reference, the following pages discuss the Group Settings and controls:
Of particular interest to our scenario is the page on Guest access:
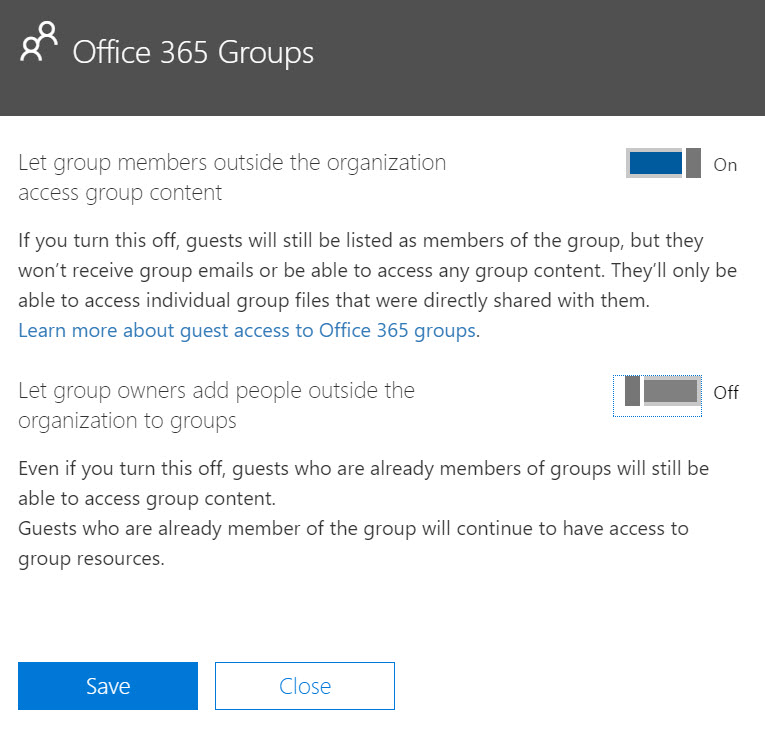
In the Security & privacy section, we need to turn off the option for users to add new guests (Figure 1).
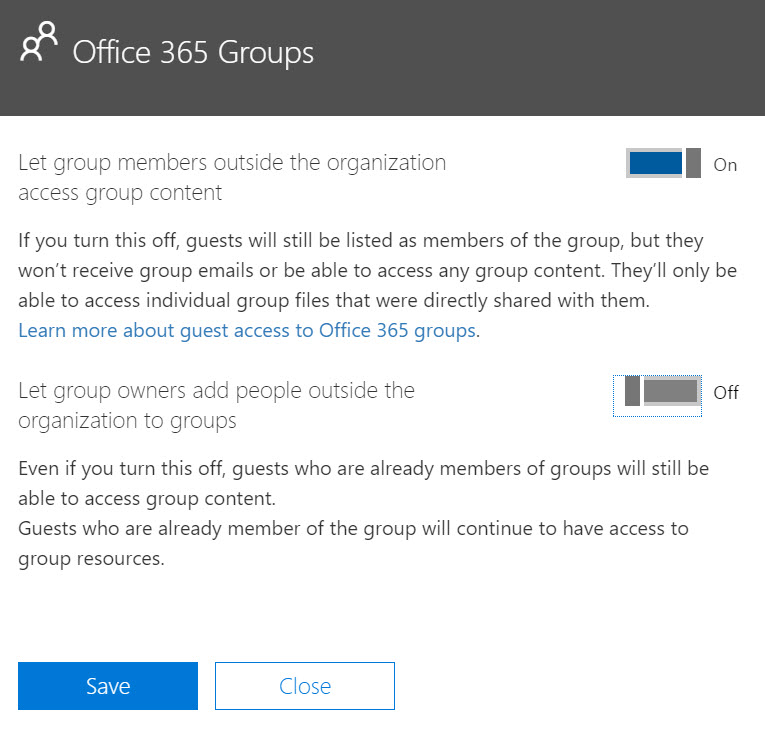
Figure 1
Reviewing the guest access options, it is clear that the option for Group Owners to add external users must be disabled. This will require Global Admins to create accounts for external users in the directory. The Group Settings required are shown in Figure 2.
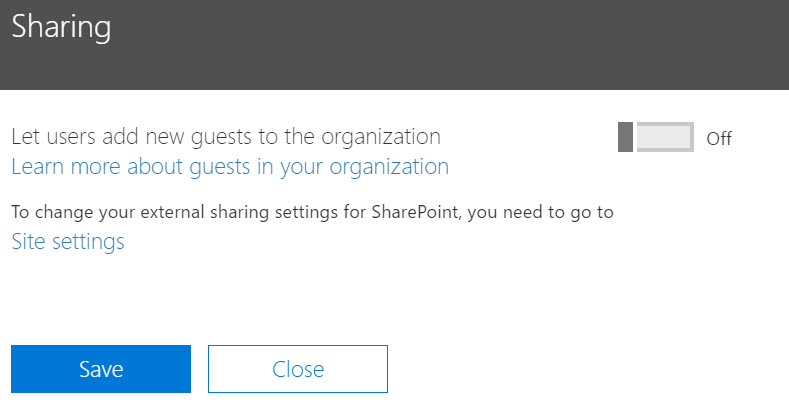
Figure 2
SharePoint Sharing settings
In addition to the Group settings for access, we must address SharePoint’s sharing capability. (This is alluded to in the Security and Privacy settings dialog in Figure 1.) The file storage and web site for a group is hosted in SharePoint. Using the SharePoint web interface, a document (or any other SharePoint item) can be shared with users. To meet our requirements, we need to restrict sharing to users that already exist. Figure 3 shows the SharePoint Admin center page for sharing, with the appropriate settings for the “Share outside your organization” section. The other sections should be reviewed and set as appropriate for your organization.
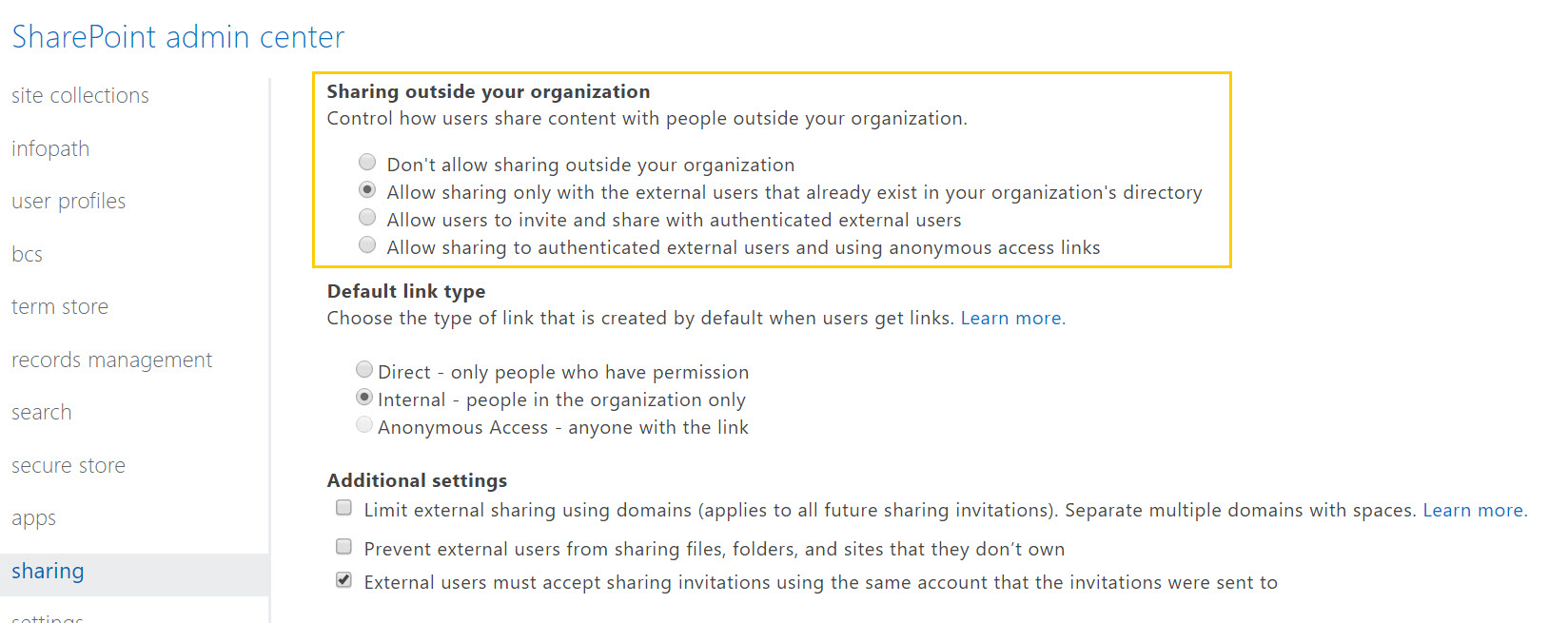
Figure 3
Creating External Users
External Users for groups (and for SharePoint) must be known to the Office 365 service. Like all user accounts, external users are added to the directory that is providing authentication services to the tenant. This directory, known as Azure Active Directory, is managed from the Azure portal.
The capability for adding guests will still display in the web interface for global administrators. However, when the invited guest tries to access the group resource, they will recieve an error. External users must be added to the directory using the Azure AD B2B Collaboration service. AAD B2B provides for uploading a CSV file describing guest accounts. For each row in the file, an invitation is sent to the user. Information on the invitation process is included in the B2B documentation. Later in this series, the invitation process will be invoked by a web service.
Group Settings via PowerShell
Making changes to the Office 365 tenant as described above is also possible using PowerShell. The Guest Access documentation page includes the prerequisites and cmdlets to do so. The Patterns and Practices group has additional cmdlets for managing office 365 Groups. Information about those cmdlets are on the Office Developer Center.